Protocol Construct
BestPath operates in shared state with Unchained, an AVS Layer 2 built on Arbitrum Orbit and MoveVM.
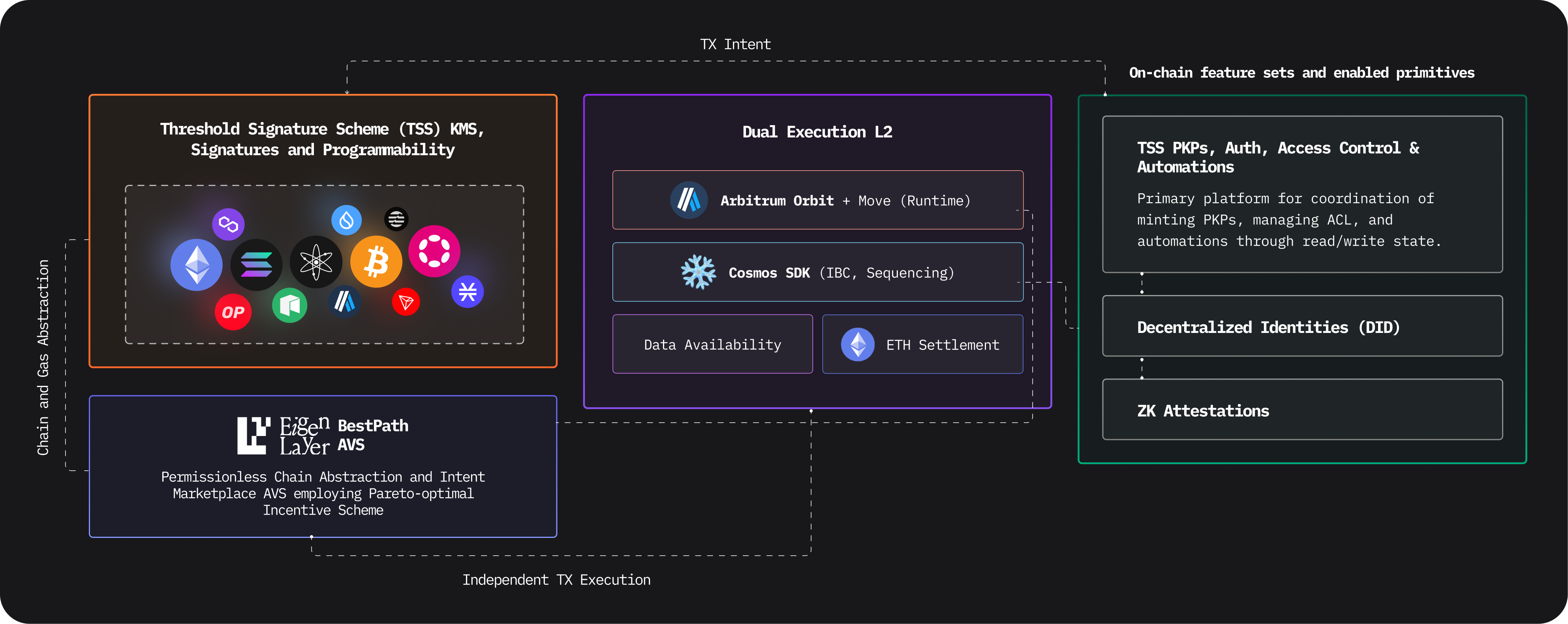
Tria's Unchained restaked L2 employs a tripartite architecture optimized for chain abstraction operations across global states and multiple virtual machine environments. The primary channel leverages a Threshold Signature Scheme (TSS) to enable verifiable, distributed signature signing, compatible with major cryptographic curves and virtual machine environments. Next, BestPath AVS serves as a permissionless chain abstraction and intent marketplace, utilizing a Pareto-optimal incentive framework to optimize global intent fulfillments. Finally, a dual-execution L2, integrates both Ethereum Virtual Machine (EVM) and Cosmos SDK, enabling the deployment of modular primitives, such as TSS-based access control, permissioning protocols, and global wallet automations under the TSS framework. Decentralized Identities (DIDs) aggregate reputation across varied state machines. Below, we will dive into a granular analysis of the constituent modules and their specific roles within Tria.
TSS Signatures and Execution
Tria adopts a novel approach to public key cryptography by leveraging Threshold Signature Schemes (TSS). TSS facilitates Asynchronous Decentralized Key Generation (ADKG) and signatures, departing from the traditional Public Key Infrastructure (PKI) reliant on centralized key custodians. Unlike PKI's single point of failure, TSS distributes key management across multiple nodes. Furthermore, Tria utilizes ADKG, ensuring no single TSS node ever possesses or reconstructs an entire private key during its lifecycle. This surpasses the limitations of Multi-Party Computation (MPC) where key reconstruction occurs during creation and signing. To bolster security beyond the inherent benefits of TSS, Tria incorporates AMD's Secure Encrypted Virtualization (SEV) - providing advanced hardware-level protection and an additional layer of security. SEV ensures that node operators never have access to any key shares directly, nor the computation processed inside of each node. This multi-layered security, detailed further in the dedicated page Security, TSS Executions and Programmability, lays the groundwork for a shared wallet infrastructure enabled by Tria's implementation of TSS over Lit Protocol (https://litprotocol.com/)
Secure Authentication and SSOs
Our TSS implementation facilitates secure login and OAuth functionality, simplifying Web3 onboarding through familiar primitives like Google, Facebook, Discord, X, mobile, offline ZK identity proofs, and other mainstream login methods. Client-side secure enclaves protect user credentials and manage session integrity, while OAuth-based logins integrate seamlessly with transaction signing, account recovery, and multi-chain logins, enabling secure, interoperable authentication across shared applications.
Portability of wallets, client-less authentication and signatures
Unlike client-dependent wallets (e.g., MetaMask) or shared-key MPC solutions (e.g., Web3Auth), Tria’s TSS implementation with client-agnostic primitives enables wallet shares to function entirely without client dependency, allowing for seamless wallet portability across devices. This architecture mirrors the fluidity and convenience of Web2 experiences such as Gmail and Venmo, delivering a familiar, frictionless user experience in Web3 environments.
Global States and Signature Curves
Tria leverages ephemeral, Lambda-like functions within Lit Protocol’s TSS network, known as Actions, to establish a fully composable signature signing framework. Operating within these ephemeral TSS actions, which supports the execution of arbitrary asynchronous functions, Tria maintains a global state of wallets across parent PKPs (Private Key Pairs). This global state enables signature signing and broadcasting across diverse virtual machines. Unlike conventional TSS-based networks with limited support for signature curves, Tria's use of Lit Actions facilitates broad compatibility, currently supporting the full spectrum of Elliptic Curve Digital Signature Algorithm (ECDSA), Edwards-curve Digital Signature Algorithm (EdDSA), Pasta among other curves encompassing the signature algorithms employed by the vast majority of blockchains refer to supported chains.
Access Control, Permissioning and Automating States
Validators running TSS nodes read and write states to Unchained L2 to facilitate granular permissioning, access control and automations of signatures to always give users a 1-click experience. This construct also enables immutable and trustless executions conditions tied to specific wallets, chain, dApp-specific actions and automated-permissions like signing a series of complex intent-based transaction.
Validator-operated TSS nodes read and write states to Unchained L2, enabling precise permissioning, access control, and automated signature workflows that deliver a seamless, one-click execution experience for end users. This architecture supports immutable and trustless execution conditions anchored to specific PKPs or children wallets, chain contexts, dApp-defined actions, and automated permissions. Through this construct, complex, intent-based transaction sequences can be programmatically authorized and executed. By embedding granular control over transaction permissions and intent routing directly within the L2, Tria facilitates trustless chain abstraction flows like multi-stage approvals, delegated signing, and condition-based automations that adhere to predefined execution rules.
Unchained AVS Layer 2
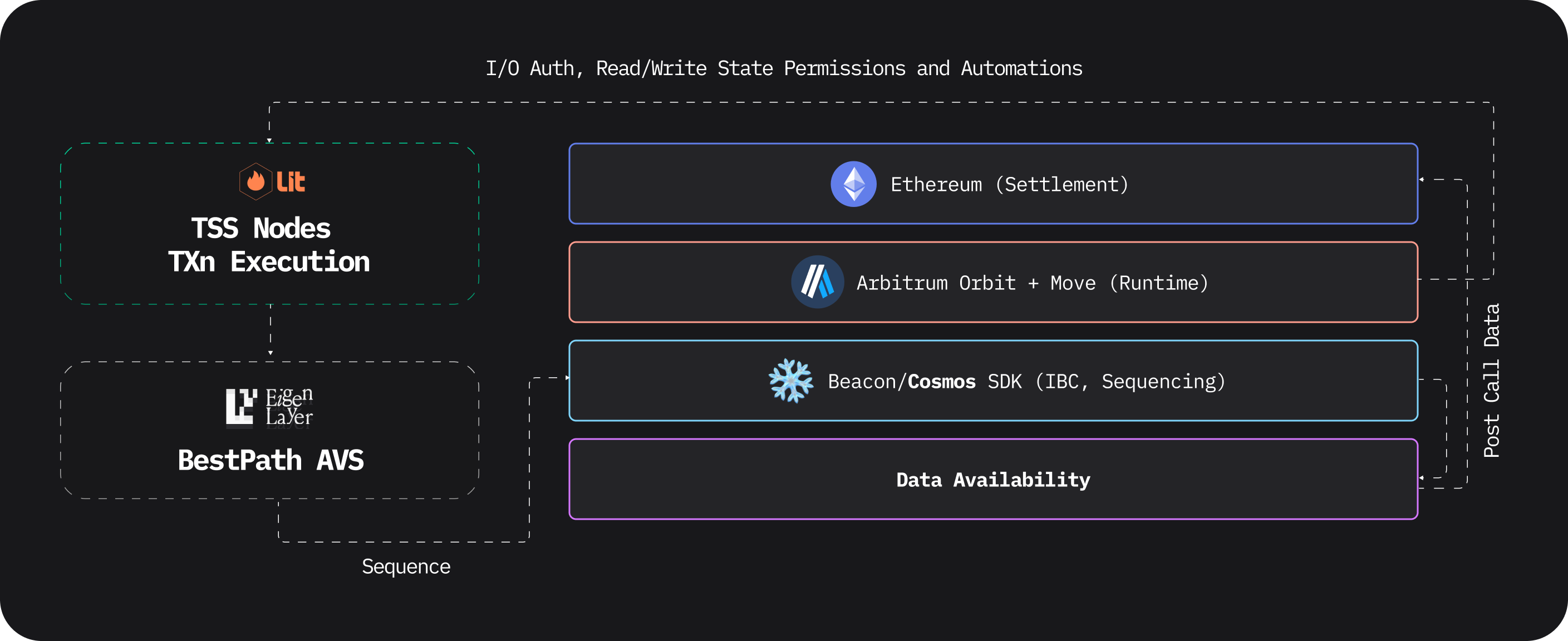
Unchained, an Arbitrum Orbit rollup, leverages a modular architecture that decouples runtime execution, state management, and settlement functions across distinct layers. Runtime and execution on Arbitrum, where Unchained sequences AVS blocks using the Cosmos SDK, handles Data Availability (DA) through Celestia, and finalizes settlements over Ethereum. Serving as the runtime layer, Unchained’s Arbitrum Orbit rollup executes core smart contract functions, including PKP generation, authentication, permissioning, decentralized identity (DID) management, and attestation services. Unchained maintains EVM-equivalence to support a broad ecosystem of libraries and ensure a familiar development environment for dApp builders working with Solidity and Move language in the future. Unchained's dual execution construct utilizes Cosmos SDK to decentralize the sequencing of blocks produced by BestPath AVS, and enables Inter-Blockchain Communication (IBC) among Cosmos blockchains, while Celestia Data Availability (DA) is utilized to store Round snapsots of BestPath blocks.
Inter-Blockchain Communication (IBC)
Inter-Blockchain Communication (IBC) is a communication protocol that enables secure and trustless communication between independent blockchains. It consists of two primary layers: the Transport Layer (TAO) and the Application Layer (APP). The TAO layer provides the core infrastructure for secure connections and data packet between chains, comprising components such as light clients, relayers, connections, and channels. The APP layer, built on top of TAO, specifies how data packets are packaged and interpreted by the communicating blockchains.
IBC guarantees reliable, ordered and authenticated communication between the chains. Blockchains can trustlessly exchange value like tokens. IBC does not work like a bridge. Instead, blockchains send packets of information via smart contracts that allow them to not only exchange value but relay any arbitrary form of data in bytes via the communication protocol.
Data Availability (DA)
Data Availability Layers (DALs) in the Web3 ecosystem serve as a critical infrastructure component, providing scalability, security, and efficiency in blockchain networks. The essence of DALs lies in their ability to ensure that data for transactions or state changes is accessible for verification without the necessity of every node storing every piece of data. This concept is particularly vital for layer 2 scaling solutions where the blockchain's main chain doesn't need to process every detail of every transaction but must be able to verify that all data is indeed available when needed.
The core mechanism behind DALs is erasure coding, where data is divided into shards, and these shards are then encoded in such a way that the original data can be reconstructed from a subset of these pieces. This approach allows a blockchain to scale by distributing data across the network in a manner that not all nodes need to store the full dataset, yet the integrity and completeness of the data can be assured. Two key features of Celestia's DA layer are data availability sampling (DAS) and Namespaced Merkle trees (NMTs). Both features are novel blockchain scaling solutions. DAS enables light nodes to verify data availability without needing to download an entire block; NMTs enable execution and settlement layers on Celestia to download transactions that are only relevant to them.
BestPath AVS
EigenLayer’s Actively Validated Service (AVS) is any distributed system requiring its own validation semantics for verification, encompassing sidechains, data availability layers, new virtual machines, keeper networks, oracle networks, bridges, threshold cryptography schemes, and trusted execution environments, among others. Each AVS operates through a distinct set of contracts that manage service-specific state, such as the identities of operators running the service and the amount of stake securing it. EigenLayer's restaking mechanism extends Ethereum’s economic security to a range of independent protocols by allowing Ethereum validators to restake their ETH or liquid staking tokens (LSTs) to support AVS computations. This pooled security model enables AVSs to benefit from Ethereum’s robust validator network, fostering a marketplace where restakers, operators, and AVS providers collaborate. In this ecosystem, operators run specialized node software to execute validation tasks for AVSs, thereby creating a decentralized infrastructure that provides economic security to diverse array of services.
BestPath AVS is a permissionless chain abstraction and intent marketplace leveraging a Pareto-optimal incentive structure. In BestPath, Pathfinders form dynamic micro-markets of modular interoperability stacks. These micro-markets enable a competitive ecosystem where solvers, fast-finality guarantors, transport layers, liquidity pools, relayers, paymasters, and other specialized actors engage in capturing, routing, and executing user intents across heterogeneous environments. By coordinating real-time orchestration of atomic execution stacks, BestPath optimizes execution to create a resilient infrastructure for seamless intent fulfillment across a wide range of environments and intent complexities. BestPath employs a Pareto-optimal incentive scheme to foster a state where user experience, permissionless developer contribution, and network efficiency are mutually reinforcing.
PathFinders compete by implementing the most effecient chain abstraction and interop strategies, with rewards tied to the demonstrably efficient execution or simulation of intents. Users benefit from the most effecient intent resolution in regards to time and capital effeiency providing a unified chain abstracted experience. Consequently, the network experiences cost minimization through effeciency. This darwinian dynamic incentivizes ongoing participation, contributing to a robust and efficient marketplace of capital effeciency and user-experience.